##前言:snort是一款最负盛名的规则匹配型的网络入侵检测系统。它具有实时数据流量分析和记录IP网络数据包的能力,能够进行协议分析,对网络数据包内容进行搜索/匹配。它能够检测各种不同的攻击方式,对攻击进行实时报警。此外,Snort是开源的入侵检测系统,并具有很好的扩展性和可移植性。
##搭建环境:
### Ubuntu 16.04 (注意:不同的系统会对snort的安装有影响)
### Snort 2.9.15 (博主安装于2019年10月,过后可能会有新版本)
##Snort的安装
---------------------------------------------------------------------------------------------------
##1. ubuntu更新
sudo apt-get update sudo apt-get dist-upgrade -y sudo apt-get install -y openssh-server sudo reboot
##2. 安装相关依赖
sudo apt-get install -y build-essential sudo apt-get install -y libpcap-dev libpcre3-dev libdumbnet-dev sudo apt-get install -y bison flex sudo apt-get install -y zlib1g-dev liblzma-dev openssl libssl-dev sudo apt-get install -y libnghttp2-dev
##3. 建立snort安装目录
mkdir ~/snort_src cd ~/snort_src
##4. 安装snort的数据库(Data AcQuisition library:DAQ)
cd ~/snort_src wget https://snort.org/downloads/snort/daq-2.0.6.tar.gz tar -xvzf daq-2.0.6.tar.gz cd daq-2.0.6 ./configure && make && sudo make install
##5. 安装snort
cd ~/snort_src wget https://snort.org/downloads/snort/snort-2.9.9.0.tar.gz tar -xvzf snort-2.9.9.0.tar.gz cd snort-2.9.9.0 ./configure --enable-sourcefire –disable-open-appid make && sudo make install
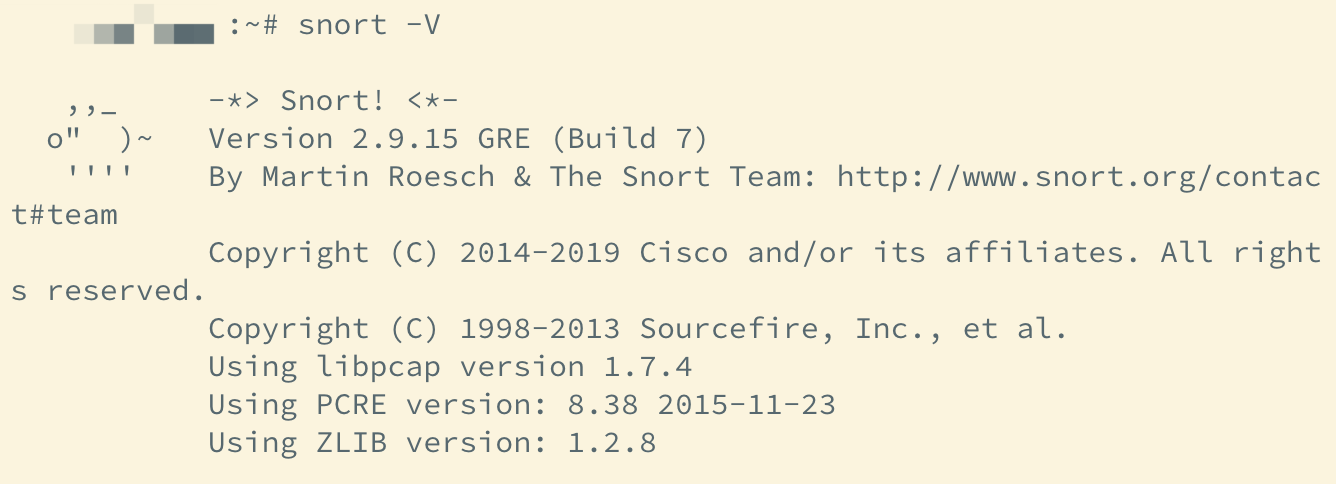
##6. 测试snort是否安装成功
snort -V //出现如下图就代表成功啦!
##Snort的网络入侵检测(Network Intrusion Detection System: NIDS)模式测试
---------------------------------------------------------------------------------------------------
##7. 配置snort需要的用户与规则库
//Create the snort user and group: sudo groupadd snort sudo useradd snort -r -s /sbin/nologin -c SNORT_IDS -g snort //Create the Snort directories: sudo mkdir /etc/snort sudo mkdir /etc/snort/rules sudo mkdir /etc/snort/rules/iplists sudo mkdir /etc/snort/preproc_rules sudo mkdir /usr/local/lib/snort_dynamicrules sudo mkdir /etc/snort/so_rules //Create some files that stores rules and ip lists sudo touch /etc/snort/rules/iplists/black_list.rules sudo touch /etc/snort/rules/iplists/white_list.rules sudo touch /etc/snort/rules/local.rules sudo touch /etc/snort/sid-msg.map //Create our logging directories: sudo mkdir /var/log/snort sudo mkdir /var/log/snort/archived_logs //Adjust permissions: sudo chmod -R 5775 /etc/snort sudo chmod -R 5775 /var/log/snort sudo chmod -R 5775 /var/log/snort/archived_logs sudo chmod -R 5775 /etc/snort/so_rules sudo chmod -R 5775 /usr/local/lib/snort_dynamicrules //Change Ownership on folders: sudo chown -R snort:snort /etc/snort sudo chown -R snort:snort /var/log/snort sudo chown -R snort:snort /usr/local/lib/snort_dynamicrules
##8. 复制所需的配置文件
cd ~/snort_src/snort-2.9.15/etc/ sudo cp *.conf* /etc/snort sudo cp *.map /etc/snort sudo cp *.dtd /etc/snort cd ~/snort_src/snort-2.9.15/src/dynamic-preprocessors/build/usr/local/lib/snort_dynamicpreprocessor/ sudo cp * /usr/local/lib/snort_dynamicpreprocessor/
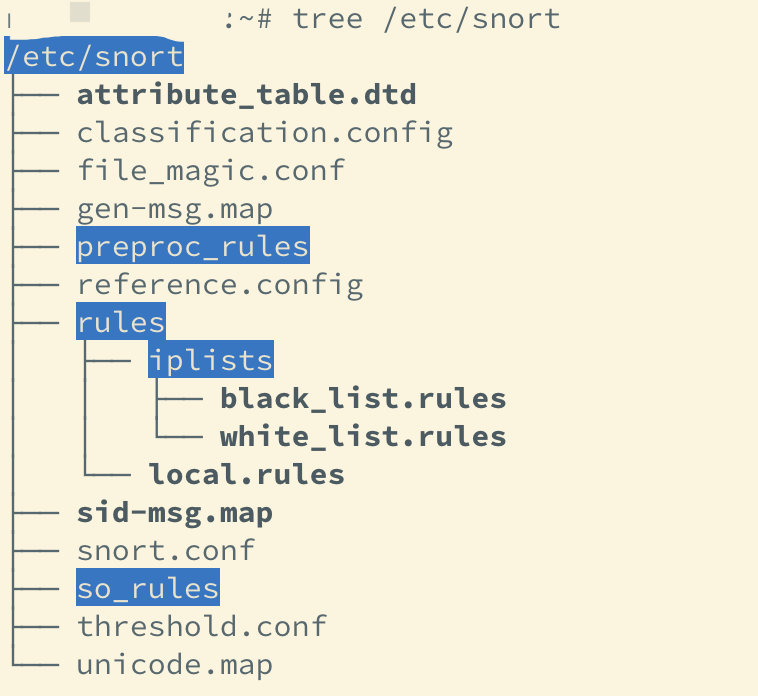
##9. 查看snort的目录
tree /etc/snort //如未安装tree,通过下面命令安装 sudo apt-get install tree
##10. 让snort以NIDS模式运行
sudo sed -i "s/include $RULE\_PATH/#include $RULE\_PATH/" /etc/snort/snort.conf
##11. 配置snort的conf文件
sudo vi /etc/snort/snort.conf //第45行,输入想要监听的ip地址 ipvar HOME_NET 10.0.0.100 //这里我的ip地址为10.0.0.100,不清楚的可以用ifconfig | grep "inet add" 查看 //第104行开始,进行如下替换: var RULE_PATH /etc/snort/rules var SO_RULE_PATH /etc/snort/so_rules var PREPROC_RULE_PATH /etc/snort/preproc_rules var WHITE_LIST_PATH /etc/snort/rules/iplists var BLACK_LIST_PATH /etc/snort/rules/iplists // 第546行,取消注释 include $RULE_PATH/local.rules
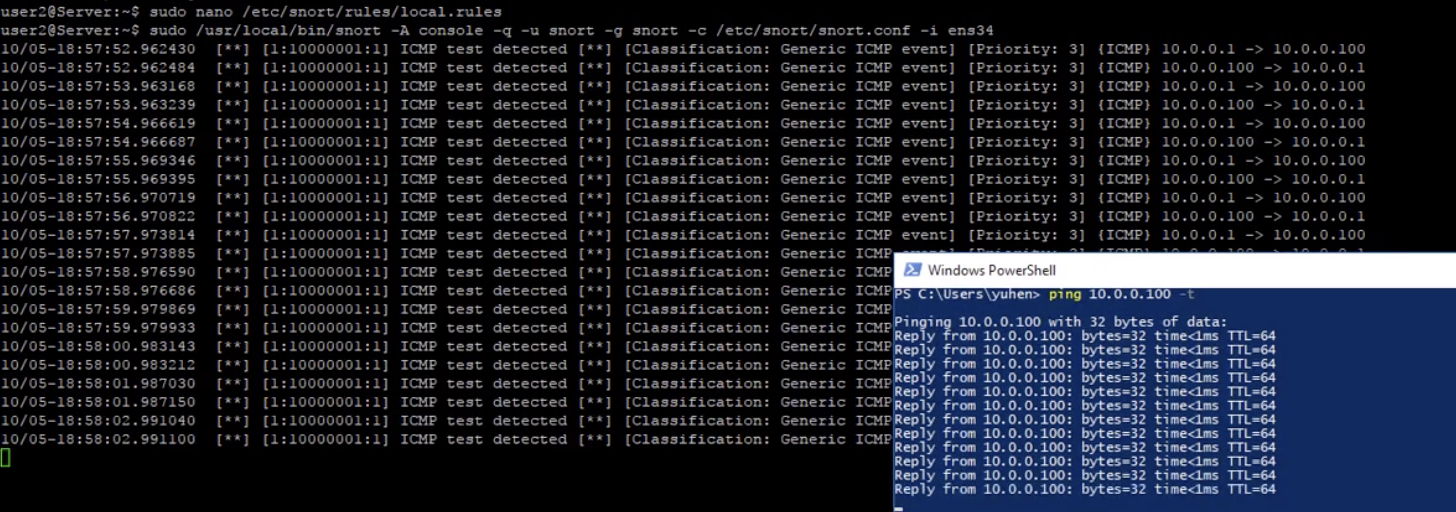
##12. 写入监听ping的最简单ICMP规则
vi /etc/snort/rules/local.rules //加入ICMP规则: alert icmp any any -> $HOME_NET any (msg:"ICMP test detected"; GID:1; sid:10000001; rev:001; classtype:icmp-event;) vi /etc/snort/sid-msg.map //加入提示消息: 1 || 10000001 || 001 || icmp-event || 0 || ICMP Test detected || url,tools.ietf.org/html/rfc792 //验证配置: sudo snort -T -c /etc/snort/snort.conf -i ens3 //有的是eth0,可以通过ifconfig来确定
##13. 运行snort,如果成功监听则代表成功
sudo /usr/local/bin/snort -A console -q -u snort -g snort -c /etc/snort/snort.conf -i ens3 //另外打开windows的命令窗口,ping对应的ip地址